
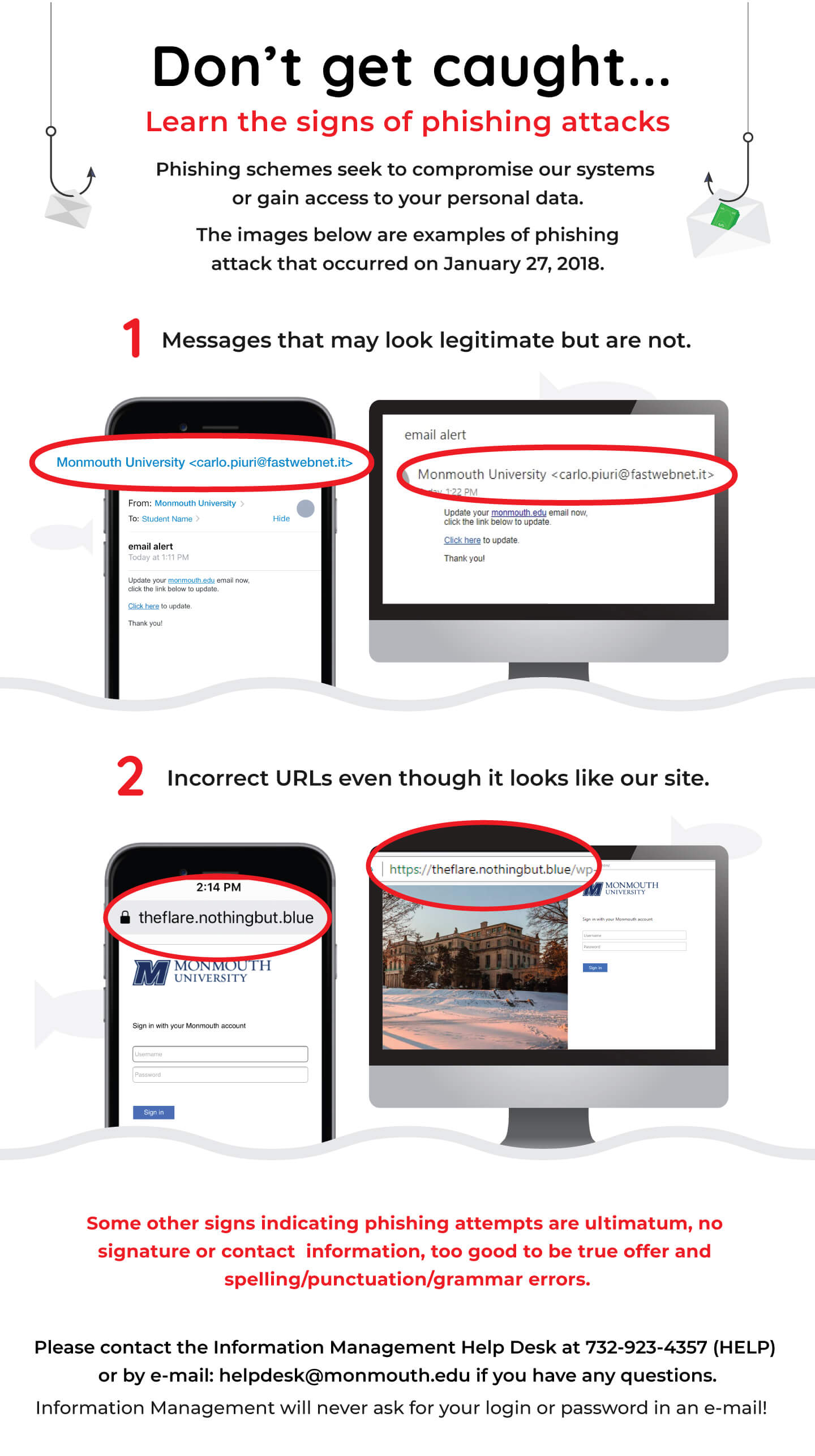
How can you tell if an e-mail message is a fraud?
Unfortunately, as phishing attacks become more sophisticated, it is very difficult to tell if a message is fraudulent. That is why phishing schemes are so prevalent and successful for criminals. For example, many phony e-mail messages link to real company logos of well-known brands; however, there are things you can be on the lookout for:
- Requests for personal information in an e-mail message.
Most legitimate businesses have a policy that they do not ask you for your personal information through e-mail. Be very suspicious of a message that asks for personal information even if it might look legitimate. - Urgent wording.
Wording in phishing e-mail messages is usually polite and accommodating in tone. It almost always tries to get you to respond to the message or to click the link that is included. To increase the number of responses, criminals attempt to create a sense of urgency so that people immediately respond without thinking. Usually, fake e-mail messages are NOT personalized, while valid messages from your bank or e-commerce company generally are. - Fake links.
Phishers are getting very sophisticated in their ability to create misleading links to the point where it is impossible for the average person to tell if the link is legitimate or not. It’s always best to type in the Web address or URL you know is correct into your browser. Also you can save the correct URL to your browser “Favorites.” Do not copy and paste URLs from messages into your browser. Some of the techniques that criminals have used in the past to fake links are as follows: - Message body is an image not text.
To avoid detection by spam filters, fake e-mail messages used in phishing schemes often use an image instead of text in the message body. If the sent spam message uses real text, the Outlook Junk E-mail Filter will very likely move the message to the Junk E-mail folder. The message body image is usually a hyperlink, you can tell because when you rest the pointer on the message body, the pointer becomes a hand. - Promises that seem too good to be true.
Use common sense and be suspicious when you are offered money or discounts that seem too good to be true.
Best practices to help protect yourself from online fraud
- Never reply to e-mail messages that request your personal information.
Be very suspicious of any e-mail message from a business or person that asks for your personal information — or one that sends you personal information and asks you to update or confirm it. Instead, use the publicly available contact information such as contacting the MU Help Desk if the e-mail is purported to pertain to a Monmouth University service. - Don’t click links in suspicious e-mail.
Don’t click a link contained in a suspicious message. Instead, visit Web sites by typing their URL into your browser or by using your Favorites link. Do not copy and paste links from messages into your browser. - Change your password regularly or if you suspect any compromise.
Once you have made the password change notify the provider of the service/account in question directly regarding the possibility of fraud or compromise. - Don’t send personal information in regular e-mail messages.
Regular e-mail messages are not encrypted and are like sending a post card, anyone whose hands it passes through can read its content. - Do business only with companies you know and trust.
A legitimate business Web site should always have a privacy statement that specifically states that the business won’t pass your name and information to other people. - Make sure the Web site uses encryption when personal information is being transacted.
The Web address should be preceded by https:// instead of the usual http:// in the browser’s address bar. Also, double-click the lock icon on your browser’s status bar to display the digital certificate for the site. The name that follows “Issued to” in the certificate should match the site that you think you’re on. If you suspect that a Web site is not what it should be, leave the site immediately and report it. Don’t follow any of the instructions it presents. - Monitor your transactions.
Review your order confirmations and credit card and bank statements as soon as you receive them to make sure that you’re being charged only for transactions you made. Immediately report any irregularities in your accounts by dialing the number shown on your account statement. Using just one credit card for online purchases makes it easier to track your transactions. - Use credit cards for transactions on the Internet.
In most locales, your personal liability in case someone compromises your credit card is significantly limited. By contrast, if you use direct debit from your bank account or a debit card, your personal liability frequently is the full balance of your bank account. In addition, a credit card with a small credit limit is preferable for use on the Internet because it limits the amount of money that a thief can steal in case the card is compromised. Better yet, several major credit card issuers are now offering customers the option of shopping online with virtual, single-use credit card numbers, which expire within one or two months. For more details, ask your bank about perishable virtual credit card numbers.


